Digital Stalking: The Risks
This page is designed to give you the information regarding your online safety. It is not designed to scare you or to make you feel that you have to limit how much time you spend on the computer or on your phone. Instead, we want to help you identify risks and work to help you minimise and manage them.
You can download our digital safety checklist here, but if your computer is shared then please delete this from your downloads folder.
If you are in immediate danger, get help now by calling our helpline on 0800 917 9948 (Mon, Tue, Thu, Fri 9am - 4.30pm) or email raisereferrals@oasisdaservice. org if it is safe to do so.
Your Digital Footprint
Every time that we go online, use our mobiles or any other kind of technology we leave behind a digital footprint. This shadow includes details of what sites we visit, who we call or speak to, the location of where we do this, details of your friends and much more.
If someone knows your passwords or usernames, the amount of information that is out there for them to access increases greatly. "Private Browsing" or "Incognito" windows can be useful when viewing information online that you do not wish to have stored on your internet history. Pages you view in incognito/private tabs won’t be available in your browser’s history, cookie store, or search history after you’ve closed all of those tabs. Any files you download or bookmarks you create, however, will be kept.
It is important to note that private browsing will not hide your browsing from your employer, your internet service provider, or from any websites you visit.
Private browsing
Once “private browsing” mode is enabled, nothing is stored about your activity on your computer in that browsing window. If you don’t know the browser you are using, click on Help on the toolbar at the top of the browser screen. A drop-down menu will appear, the last entry will say About Internet Explorer, About Mozilla Firefox, About Google Chrome or something similar. The entry refers to which browser type you are using – you should then refer to the relevant instructions below.
Internet Explorer: Go to Safety – Tools – “InPrivate Browsing”.
Firefox: Click the Menu button with three horizontal lines – “New Private Window”.
Chrome: Click the Menu button with three horizontal lines and select “New Incognito Window”.
Deleting your browsing history
Internet browsers keep a record of all the web pages you visit. This is known as a ‘history’. To delete history for Internet Explorer and Firefox hold down the Ctrl key on the keyboard, then press the H key (Ctrl, Alt and H for Opera). Find any entries that say www.oasisdaservice.org.uk, right click and choose Delete. For Google Chrome, go to the three dots in the top right of the toolbar, select ‘Settings’ and go to ‘Clear browsing data’
Computer Spyware
Computer spyware is a growing trend and becoming more accessible as it is easy and completely legal to buy. Computer spyware is software which allows the person who has installed it to watch what a computer is doing; in some instances this can mean watching it live as you visit websites, read what you type and literally see what you see.
The software is very easy to install and can be done either manually with physical access to your computer or via email attachment that once opened uploads the software without your knowledge.
Until you have run anti-spyware software through your computer, you should assume that it has been tampered with and is therefore unsafe.
You can install free anti spyware software for your Windows computer by visiting www.windows.microsoft.com/en-US/windows7/products/features/windows-defender. It is completely free and gives you a step by step guide of how to install the protection software.
If you have an Apple Mac computer you may use the following anti-virus and spyware software http://www.avg.com/gb-en/avg-antivirus-for-mac which is also free and easy to use.
Social Engineering
Social Engineering is effectively confidence tricking through technological means. A person can find out things about you by using basic information that they have found either via your digital footprint or via non-safe social networking sites. For example;
Sarah posted on her facebook page “Can’t believe I have been waiting at the doctors for an hour just to get my prescription”. Dan, Sarah’s brother commented on her status “That’s awful! Doctors are terrible round here!” Steven, Sarah’s ex can see that Dan commented on Sarah’s status that she has been to the doctor's. Steven then called Dan pretending to be the doctors asking for Sarah’s new number to give her test results. Dan, meaning well, gives it to him.
Social Engineering can also include tricking a person to give out their passwords or bank details.
Mobile Phone Safety
There are a number of ways that mobile phones can be threatened.
Mobile Spyware
Similar to computer spyware, mobile spyware is designed to give access to your phone without having to be in the physical presence of it. It can allow the person who installed the spyware to: listen in to your calls, control the functions of your phone, send copies of all your text messages to the spy’s email account, intercept calls, block calls without you knowing and hide all contact from selected numbers.
You can remove mobile spyware by returning your phone to its original factory setting, which is usually an option under your phone’s settings or options. (Make sure that any app purchases are backed up before you do this otherwise you will lose your saved data.)
Geolocation
This uses local signal masks to locate your phone at any one point. Usually this is only done by mobile phone operators but they are legally able to sell this for the purposes of monitoring children etc.
Geotagging
This is when a phone captures where it is at any one point and attaches this location to an update, an email or a photo. There is also the danger of Google Panoramio and other similar sites. These sites add your photo to Google Maps in the area that they were taken. (For example; if you uploaded a photo which was geotagged to Ramsgate, if you searched Ramsgate in the Google Maps- your photo could come up.)
The Frequent Locations system on iPhones pinpoints the places you go on a map, how many times you’ve paid a visit, and the exact times of your arrival and departure. Anyone with access to your phone can set up Find My Friends and view your every move.
How to turn off Frequent Locations:
Launch the Settings app from the Home screen of your iPhone or iPad.
Tap on Privacy.
Now tap on Location Services at the top.
Towards the bottom of the next screen, tap on System Services.
Again, towards the bottom of the next page, tap on Frequent Locations.
At the top of the next screen, turn the Frequent Locations option to the Off position.
This process is similar on other phones, you can very simply turn off Geotagging and Geolocation by changing your location preferences in your phone’s settings and pressing to disable finding your GPS location.
Social Network Sites (Facebook, Instagram, Twitter)
When moving to a new place, facebook and similar sites can be a good way to keep in touch with your friends and family. The problem is however, that someone who wants to find out information on you and track what you are doing or where you are living will also know this and may look to exploit it. Unless your privacy settings, and all of your friends’ privacy settings and all of their friends’ privacy settings (and so on and so on) are high, then leaks of information will happen.
If you have not disabled Geotagging or Geolocation, every time that you post a status to facebook it will post your location as well. You are able to disable location settings for one app and not for another. Therefore you may still wish to use Google Maps or another app which needs your location, but social media sites will not be able to publish your location.
Make sure your set Privacy settings
When you block someone on Facebook or Instagram, they will no longer be able to search for your profile.In order to make it harder for someone you’ve already blocked from contacting you again through a new Instagram account, when you block someone you now have the option to both block their account and preemptively block new accounts that person may create.
Messenger now allows you to ignore a conversation and automatically move it out of your inbox without having to block the sender.
You can control who can comment on your public posts on Facebook.
All UK Instagram accounts now have the ability to filter private message requests containing offensive words, phrases and emojis. These can also be added to your comment filter, meaning no comment containing these terms will appear under your posts.
Instagram’s new Sensitive Content Control tool allows you to decide how much sensitive content shows up in the ‘Explore’ tab.
More information on how to use these controls can be found here.
Instant Messaging Applications (Snapchat, Whatsapp, Kik)
Instant messaging applications often have all privacy settings disabled when you first make an account. This means that your information, profile picture, and name are often available to anyone using that site unless you actively change this. For most applications it is as simple as accessing settings and then selecting privacy and choosing which information you wish to remain private and what you may wish to share.
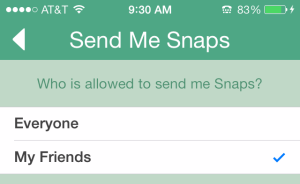
With Snapchat you can customise who can send you "snaps" and see your "stories" in settings. Set "Who Can Send Me Snaps" to either 'Everyone' or 'My Friends' and "Who Can View My Story" to either 'Everyone,' 'My Friends,' or 'Custom'. By default, only users you add to your friends list can send you Snaps. If a Snapchatter you haven't added as a friend tries to send you a Snap, you'll receive a notification that they added you, but you will not receive the Snap they sent unless you add them to your friends list.
With every instant messaging application it is paramount that you ensure you know who is on your friends list and has access to your information. However with Snapchat it is also important to note that anyone can take a screenshot of a "Snap", or simply use another camera to take a picture of a "Snap" that appears on their screen.
These risks are not exclusive to victims of domestic violence as they are real to any person that uses a mobile phone or the internet. Some of the risks may apply to you more than others, and some might not at all. However, it is better to assume that you are at risk and work to manage and minimise any potential issues to ensure that you can continue to live free from intimidation and harassment.
If an abuser sends you threatening or harassing email messages, they may be printed and saved as evidence of this abuse. Any email you have previously sent will be stored in Sent Items. If you started an email but didn’t finish it, it might be in your Drafts folder. If you reply to any email, the original message will probably be in the body of the message – print and delete the email if you don’t want anyone to see your original message.
When you delete an item in any email program (Outlook Express, Outlook, etc.) it does not really delete the item – it moves the item to a folder called Deleted Items. You have to delete the items in deleted items separately. Right click on items within the Deleted Items folder to delete individual items.
Technology can also help make you safer
One example of this is the Hollie Guard App which turns your smartphone into an advanced personal safety device at the touch of a button. If in danger simply shake your phone to generate an alert, your location, audio and video evidence of the incident will automatically be sent to your emergency contact via text and email. Shake it again and it sends out a high pitched alarm and the flash starts to strobe, in order to attract maximum attention.
Revenge porn and sharing intimate images without consent
It is illegal to share or threaten to share revealing or intimate videos or pictures of someone without their consent. If you have been the victim of this offence you can call the Revenge Porn helpline on 0345 6000 459 (Tuesday - Thursday 10 - 4pm) or visit www.revengepornhelpline.org.uk. You can also talk to us about your relationship.
If you’re under 18 and a nude image or video of you has been shared online, you can report it to be removed from the internet, Childline can help you to get the image removed.
FOR NON-EMERGENCY SUPPORT AND SAFETY PLANNING:
CALL OASIS’S EAST KENT AND MEDWAY HELPLINE:
0800 917 9948
(Mon, Tue, Thu, Fri 9am - 4.30pm. Closed 24 - 27 & 31 December, 1 & 2 January)
Or email helpline@oasisdaservice.org
(if it’s safe to do so)
For 24/7 support call the national helpline
0808 2000 247